As the digital commerce grows more complex, businesses face increasing security challenges, particularly when it comes to web applications. These applications are crucial for engaging with customers, processing payments, and storing sensitive data. To address these challenges, the Payment Card Industry Security Standards Council (PCI SSC) introduced Version 4.0 of the PCI Data Security Standard (PCI DSS). This update, which went into effect on March 31, 2024, enforces new requirements designed to protect payment scripts and webpages, placing more emphasis on securing client-side activities. In this article, we’ll explore how behavior-based security solutions, such as Source Defense Protect, can help organizations achieve compliance with these latest PCI DSS requirements. The deadline for implementation is March 31, 2025.
The Essentials of PCI DSS and Why It Matters
PCI DSS is a global security standard that ensures businesses handling credit card information protect their customers’ data.This focuses on detecting unauthorized changes to web applications. Organizations must implement solutions that continuously monitor for any modifications to critical code or configurations that could expose vulnerabilities or compromise sensitive data.
Behavior-Based Defenses: A Modern Approach
Behavior-based web application defenses take a unique, forward-thinking approach to protecting web applications. These solutions focus on monitoring real-time behavior of web applications and scripts, allowing them to detect unusual or malicious activities. Solutions like Source Defense Protect offer this behavior-based protection, providing an adaptable and effective means of securing web applications against evolving cyber threats.
Why Behavior-Based Solutions Stand Out
In contrast to more traditional security controls such as Content Security Policies (CSP), behavior-based defenses offer several important benefits:
- Real-Time Threat Prevention: By continuously monitoring the behavior of web applications, these defenses can quickly detect and stop security threats before they become significant issues.
- Flexibility and Adaptability: Behavior-based solutions can adapt to changes in web applications or new threats automatically, offering ongoing protection without the need for constant updates or manual adjustments.
- Simpler Deployment: Compared to static policies like CSP, behavior-based solutions are typically easier to deploy and manage, making them more accessible for organizations with limited security expertise or resources.
- Enhanced User Experience: These solutions minimize disruptions to users by reducing false positives that may block legitimate actions, ensuring a smooth experience without compromising on security.
Aligning Behavior-Based Solutions with PCI DSS
For organizations aiming to meet PCI DSS standards, behavior-based solutions offer an effective way to ensure compliance. With Requirement 6.4.3, these solutions can monitor scripts in real-time to prevent unauthorized execution and ensure that only verified scripts are allowed to run on payment pages. This capability effectively meets the requirement for script management and verification.
For Requirement 11.6.1, behavior-based defenses continuously check for unauthorized changes to web applications, monitoring the integrity of the code in real-time. This approach allows organizations to detect any unapproved alterations that might put payment data at risk, thereby helping to prevent breaches and ensure regulatory compliance.
Given the fast-moving cybersecurity threat landscape, organizations must adopt innovative, adaptive security strategies to protect their web applications. Behavior-based defenses, like Source Defense Protect, are well-suited to meet these needs. They not only enhance protection against emerging threats but also simplify the path to PCI DSS compliance. By implementing these advanced solutions, organizations can safeguard their client-side web applications, maintain compliance, and provide a secure online experience for their users.
With the right combination of real-time monitoring, adaptability, and ease of use, behavior-based defenses are paving the way for a safer and more secure digital environment, offering businesses peace of mind in the face of ever-evolving cyber risks.
A Walk Through – How It Works
Observation of Security Breach: Key Logging Unauthorized Script Execution Below is an example of a key logger attack running on an unprotected site. A malicious script was executed and then characters were typed into the web application and the keystrokes were logged.
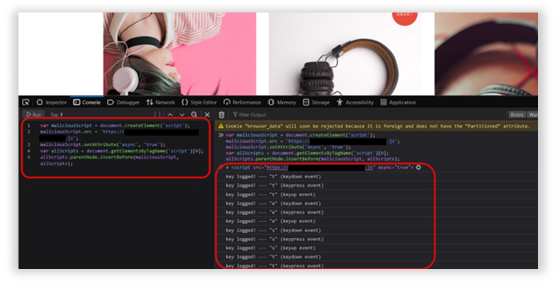
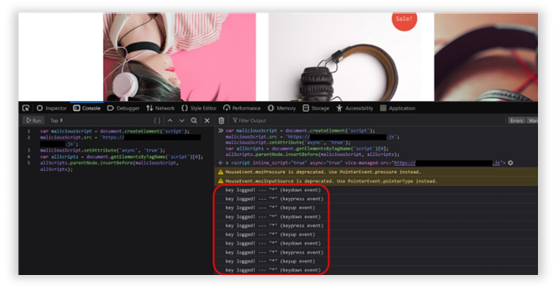
In the screenshot below, the attack is running against a site that has Source Defense Protect deployed. Note that Source Defense Protect actively redacted characters within the script to prevent data leakage.
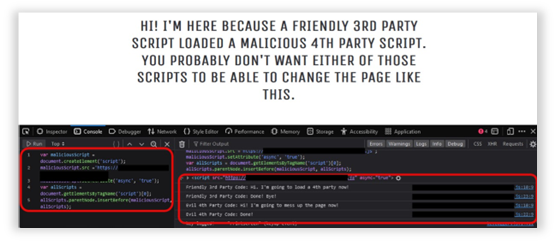
Observation of Security Breach: Supply Chain Unauthorized Script Execution
The example below shows an authorized third-party script running on an unprotected website. The example demonstrates the infiltration of a malicious script on the system, leading to unintended modifications on the website
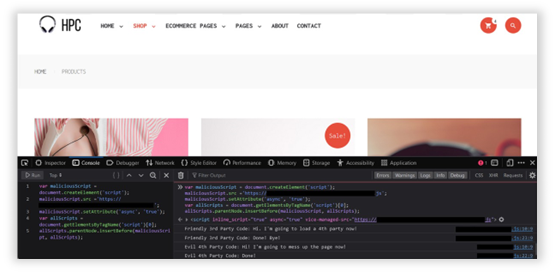
Once the solution is deployed and running the test again, as shown below Source Defense Protect effectively blocked the attack and prevented the website from being modified.
Source Defense Protect
Source Defense Protect can be deployed via the configuration of two lines of code positioned at the header of the HTML page. This script enabled the transmission of data through the solution, facilitating the monitoring and if configured correctly, the blocking of potential client-side attacks.
Configuration:
Source Defense Protect allows for two site-wide settings.
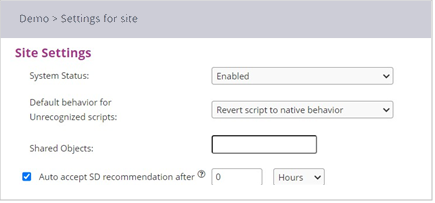
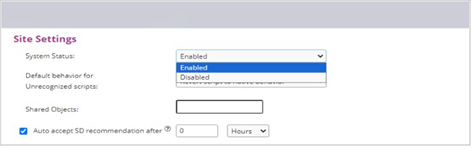
First, the site can be configured as Enabled/Disabled, which serves as a primary “Kill Switch” as seen below: (Default state is “Enabled”
Next the “Default behavior for Unrecognized scripts” can be configured at a site level as well
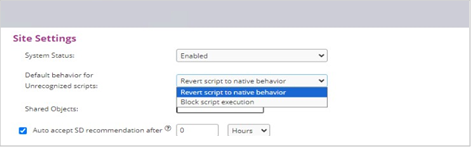
Source Defense Protect can be configured to “Revert script to native behavior” which allows unrecognized scripts to run without interference. The second option “Block script execution” disables any unrecognized scripts. Initially, Source Defense Protect is configured to the “Revert script to native behavior” mode. The system can also be set to auto-accept policy recommendations from Source Defense within a defined frequency.
The solution can be deployed at the script level in different modes, as detailed below:
Initially, Source Defense Protect configures all scripts to a temporary mode referred to as “Identified” as it identifies scripts used on the website as noted in the screenshot below. During this temporary window, Source Defense support personnel review the scripts and provide recommended policies.
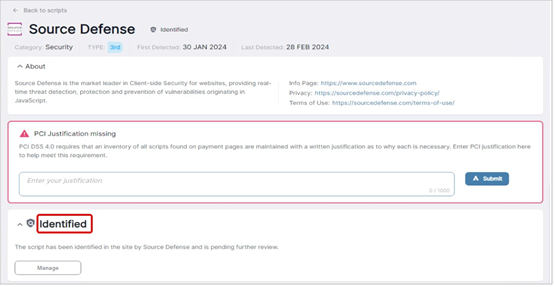
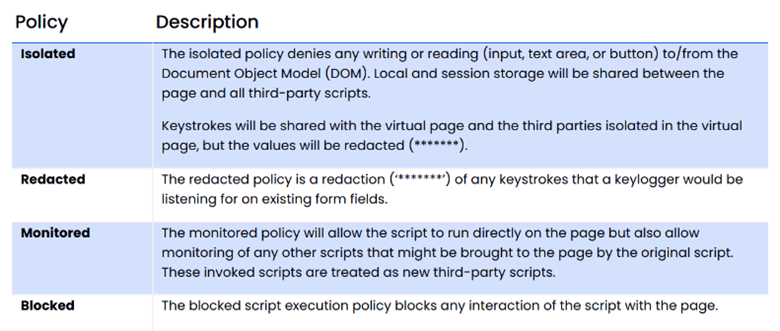
By default, Source Defense support personnel monitor the script identification process and provide recommendations on actions for each script (such as setting the script to “Isolated” or “Redacted.”) By default, the application will apply the Source Defense recommendations unless the customer specifically sets a different mode for a given script. Identified first party scripts are set to “Monitored” mode, pending review with the customer. In Monitored mode the application allowed scripts to run natively while monitoring which scripts are running on the website.
All 2nd, 3rd, or nth party scripts are configured to “Isolated” mode by default. Identified scripts can also be configured in “Redacted” mode which ensures the removal of sensitive information, such as keystrokes being sent to a keylogger, while not implementing the full limitations of “Isolated” mode. This mode may be useful in certain situations where there is a business or technical constraint that running the script in “Isolated” mode would result in functional or operational impact.
Finally, scripts can be set to “Blocked” mode which fully removes the ability of script execution.
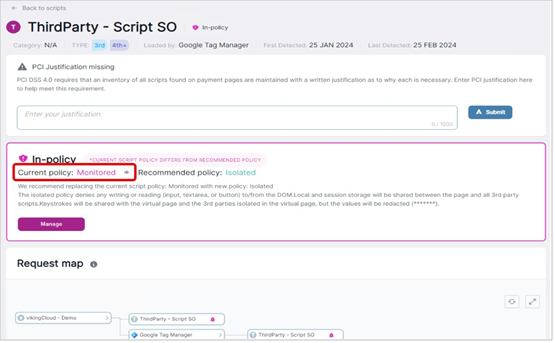
Newly identified scripts are set to ”Monitored.”
Scripts can then be configured to ”Isolated”” mode as shown below:
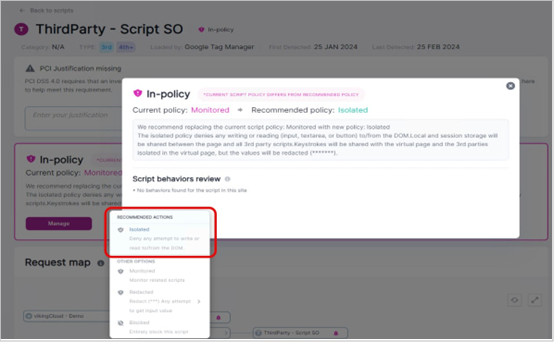
“Isolated” mode can be selected as the policy to provide protection for this script.
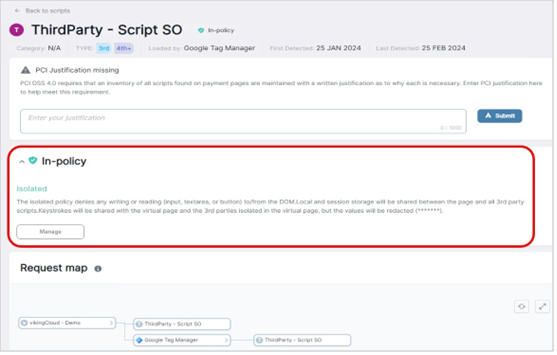
The script is now protected in ”Isolated” mode.
In isolated mode script functionality is limited to authorized behavior
Dashboard
Customers using Source Defense Protect have access to a dashboard that may provide visibility into identified issues and offers the flexibility to adjust the solution according to their requirements.
Sample dashboard as captured during testing
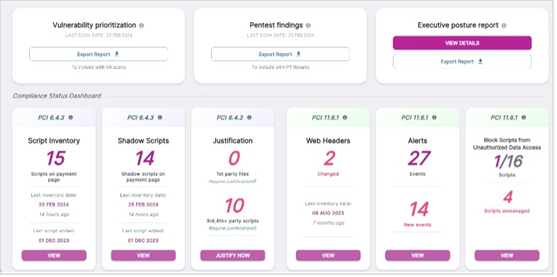
Supporting Compliance With 6.4.3 and 11.6.1:
The Source Defense Protect solution, configured in “Redacted” or “Isolated” mode for specific website scripts, delivers powerful protection that fully meets PCI DSS requirements 6.4.3 and 11.6.1. Rigorous technical evaluations and testing confirm that, when deployed correctly, Source Defense Protect safeguards against unauthorized script execution and prevents changes to web-facing applications. By integrating Source Defense Protect, your organization can effortlessly meet critical PCI DSS requirements while enhancing overall web security with an additional protective layer for your applications.
Request your FREE PCI 4.0 Compliance Analysis Report: for Requirements 6.4.3 and 11.6.1 for Your Website and On-Line Payments
What Is Included with The FREE Analysis and Assessment:
We provide an initial report of your current inventory and how it aligns with various PCI requirements. You will receive a free analysis report. After that, you can upgrade to the full-featured Detect and PROTECT edition.
** Disclaimer: Depending on the complexity of your payment page workflow, we may not be able to accommodate the Free Analysis and Report for all use cases. However, we will demonstrate how the process would work for your specific requirements.
We’re Here to Help
Call 1 800 831 6660 or
What our clients are saying about us
“Never any issues with you guys! Things just work.”
“Customer service is a really big deal to us, and I am glad to do business with a company that obviously takes it as seriously as we do.”
“We’re happy with the IVR Payment system and it has been working well for us. Recently we also setup your newest SMS (text) receipts and found it to work great.”
“I want to command you and your team at Datatel on the job just completed for Tele-Response Center. The attention to detail and professionalism with which you approached the project was exemplary and greatly appreciated especially considering the several applications that needed to be implemented on short notice. Thanks again for your assistance getting this project off the ground so smoothly.”
“My team and I would like to commend Datatel on creating an IVR application that adds great value to our new Travel product. Your knowledge, input and expertise in IVR scripting, call flow management and overall IVR logistics made the development and implementation stages extremely easy to manage. Thank you for a well executed campaign that was launched on time and on budget.”
“Great team to work with. I look forward to utilizing some additional capabilities in the future.”
“We are very grateful for many years of mutually beneficial business relationship with Datatel and for impeccable customer service we have received during these years.”
“We, Standard Life, very much appreciated Datatel’s expertise, knowledge and support as we worked through the development and implementation stages. Our Clients appreciate the simplicity of the capability, while gathering very valuable feedback. Thanks for making this a very positive experience.”
“This was one of the best implementations I have been a part of. The communication was excellent and everything was responded to and dealt with swiftly. A real pleasure. We are looking forward to the impact this will have on our patient payments! Thank you!”